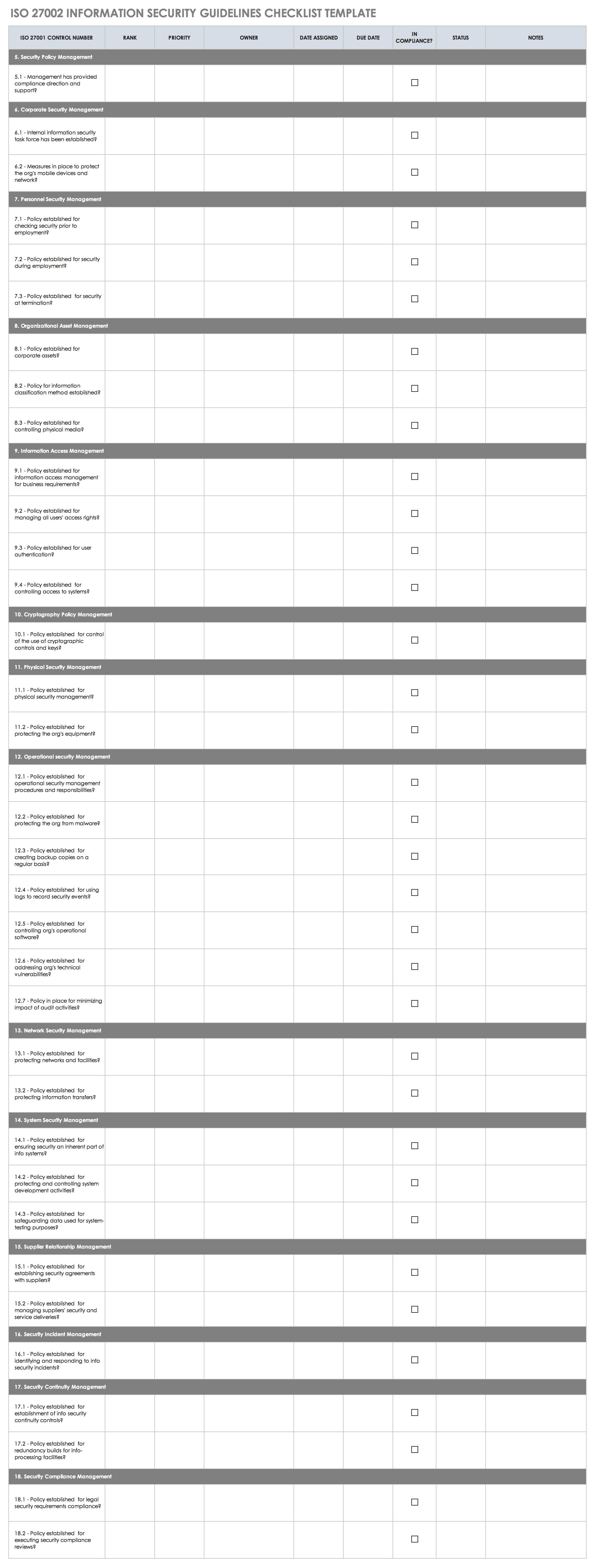
Several people have asked for an IT Audit Program Template for an audit based on the ISO/IEC 27002:2005(E) security standard. This template, which can be found here
ISO/IEC 27002 is an information security standard published by the International Organization for Standardization (ISO) and by the International Electrotechnical Commission (IEC), titled Information technology – Security techniques – Code of practice for information security controls. ISO/IEC 27002 was prepared by Joint Technical Committee ISO/IEC JTC 1, Information technology, Subcommittee SC 27, IT Security techniques. This first edition of ISO/IEC 27002 comprises ISO/IEC and ISO/IEC /Cor.1:2007. Its technical content is identical to that of ISO/IEC. ISO/IEC /Cor.1:2007 changes the.
[download]
Iso 27002 Standards
will help you in your assessment of an organization’s information security program for CobiT Maturity Level 4.
CobiT Maturity Level 4 Managed and Measurable, states that the status of the Internal Control Environment is “There is an effective internal control and risk management environment. A formal, documented evaluation of controls occurs frequently. Many controls are automated and regularly reviewed. Management is likely to detect most control issues, but not all issues are routinely identified. There is consistent follow-up to address identified control weaknesses. A limited, tactical use of technology is applied to automate controls.”
CobiT Maturity Level 4 Managed and Measurable, states that for the Establishment of Internal Controls; “IT process criticality is regularly defined with full support and agreement from the relevant business process owners. Assessment of control requirements is based on policy and the actual maturity of these processes, following a thorough and measured analysis involving key stakeholders. Accountability for these assessments is clear and enforced. Improvement strategies are supported by business cases. Performance in achieving the desired outcomes is consistently monitored. External control reviews are organized occasionally.”
As an example, one of the questions in the section on “Allocation of information security responsibilities” is written as follows:
Are the assets and security processes associated with each particular system identified and clearly defined?
Iso 27002 Controls
While this is a straightforward “yes” or “no” question, in order to answer that question the IT auditor would need to look at an organization’s Business Impact Analysis and verify that the assets and security processes were indeed identified and clearly defined.
You will also notice that I have cross-referenced each of the steps to the appropriate sections within CobiT.
I hope the template ISO27002 Security Framework will be of assistance to you.
Iso 27002 Checklist Xls
Kenneth